Cloud Migration Strategy Services
Move to the cloud with a clear, secure strategy.
Our cloud migration strategy services ensure smooth transitions with minimal downtime and risk.
Comprehensive Cloud Migration Approach
Our proven methodology ensures secure, compliant, and cost-effective cloud migrations tailored for healthcare organizations.
Discovery & Assessment
Comprehensive analysis of current infrastructure, applications, and dependencies to create detailed migration roadmap.
Security & Compliance
Supporting HIPAA Compliance migration with encryption, access controls, and protected health information handling protocols.
Optimization & Monitoring
Continuous optimization with cost management, performance tuning, and 24/7 monitoring capabilities.
Why Choose Our Cloud Migration Strategy?
- Healthcare-specific expertise with Supporting HIPAA Compliance built-in
- Proven methodology with 200+ successful healthcare migrations
- Zero-downtime migration approach with rollback capabilities
- Cost optimization strategies reducing cloud spend by 30-40%

Business Objectives and Success Criteria
Define clear, measurable outcomes that align cloud migration with your healthcare organization's strategic goals.
Cost Reduction
Reduce infrastructure costs by 30-40% through optimized resource allocation and cloud-native services
Scalability & Performance
Enable elastic scaling and improved performance to handle varying healthcare workloads
Security & Compliance
Enhance security posture while maintaining Supporting HIPAA Compliance and data protection standards
Business Continuity
Improve disaster recovery capabilities and ensure 99.9% uptime for critical healthcare systems
Success Measurement Framework
Performance KPIs
- Application response time
- System availability
- User satisfaction scores
- Incident resolution time
Financial Metrics
- Total cost of ownership
- Operational cost reduction
- Resource utilization rates
- ROI achievement timeline
Compliance Metrics
- HIPAA audit results
- Security incident count
- Data breach prevention
- Regulatory compliance score
Current State Discovery
Comprehensive assessment of your existing infrastructure, workloads, dependencies, licensing, and costs to inform migration strategy.
Workload Analysis
- Application inventory and dependencies
- Performance baselines and resource utilization
- Integration points and data flows
- Business criticality and availability requirements
Infrastructure Assessment
- Server specifications and capacity
- Network topology and bandwidth
- Storage systems and data volumes
- Security controls and access patterns
Licensing & Costs
- Software license inventory and terms
- Current infrastructure costs
- Support and maintenance contracts
- Vendor relationship analysis
Dependencies Mapping
- Application interdependencies
- Database relationships
- External system integrations
- User access patterns and workflows
Discovery Process & Timeline
Planning
Scope definition and tool deployment
Week 1
Data Collection
Automated discovery and manual assessment
Weeks 2-3
Analysis
Data analysis and dependency mapping
Week 4
Reporting
Findings presentation and recommendations
Week 5
Discovery Deliverables
Comprehensive documentation package including current state assessment, migration readiness report, and detailed recommendations.
Target Architecture Design
Design secure, scalable cloud architecture with proper landing zones, network segmentation, security boundaries, and identity management.
Landing Zones
Pre-configured, secure environments for workload deployment
- Multi-account structure
- Governance policies
- Baseline security
- Network isolation
Network Design
Secure, scalable network architecture with proper segmentation
- VPC design
- Subnet planning
- Security groups
- Load balancing
Security Boundaries
Defense-in-depth security model with multiple protection layers
- Encryption at rest/transit
- Access controls
- Monitoring
- Compliance frameworks
Identity & Access
Centralized identity management with role-based access control
- Single sign-on
- Multi-factor auth
- Role definitions
- Privilege management
Cloud Architecture Patterns
Multi-Cloud Strategy
Leverage multiple cloud providers for redundancy, cost optimization, and vendor independence.
Hybrid Architecture
Seamless integration between on-premises and cloud environments for gradual migration.
Microservices Design
Containerized, scalable architecture enabling independent service deployment and scaling.
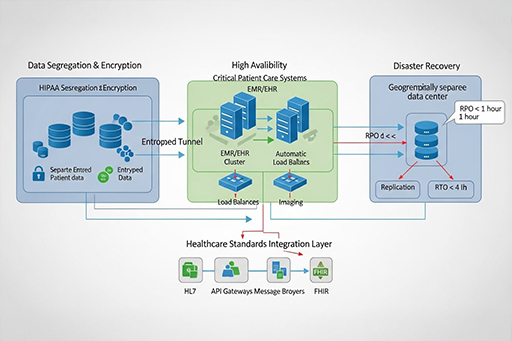
Healthcare-Specific Architecture Considerations
- Supporting HIPAA Compliance data segregation and encryption
- High availability for critical patient care systems
- Disaster recovery with RPO/RTO requirements
- Integration with healthcare standards (HL7, FHIR)
Migration Approach & Decision Matrix
Choose the right migration strategy for each workload: rehost, refactor, replatform, or retire based on business requirements and technical constraints.
Rehost (Lift & Shift)
Move applications to cloud with minimal changes
Key Benefits
- Quick migration
- Minimal risk
- Immediate cloud benefits
Best For
Replatform
Make targeted optimizations during migration
Key Benefits
- Performance gains
- Cost optimization
- Cloud-native features
Best For
Refactor
Redesign applications for cloud-native architecture
Key Benefits
- Maximum optimization
- Scalability
- Innovation enablement
Best For
Retire
Decommission applications no longer needed
Key Benefits
- Cost reduction
- Simplified architecture
- Reduced maintenance
Best For
Decision Matrix Framework
| Criteria | Rehost | Replatform | Refactor | Retire |
|---|---|---|---|---|
| Migration Speed | Fast | Medium | Slow | Fastest |
| Cost Optimization | Low | Medium | High | Highest |
| Technical Risk | Low | Medium | High | Lowest |
| Future Scalability | Limited | Good | Excellent | N/A |
Migration Strategy Recommendations
Our experts analyze each workload against multiple criteria to recommend the optimal migration approach, balancing speed, cost, risk, and long-term benefits.
Data Movement Plan
Comprehensive strategy for moving datasets with proper sequencing, bandwidth planning, and change freeze windows to ensure secure, efficient data migration.
Data Discovery
1-2 weeks- Data inventory and classification
- Volume and growth analysis
- Dependency mapping
- Compliance requirements review
Sequencing Strategy
1 week- Migration wave planning
- Dependency-based ordering
- Risk assessment and mitigation
- Rollback planning
Bandwidth Planning
1 week- Network capacity assessment
- Transfer time calculations
- Optimization strategies
- Parallel transfer planning
Change Management
Ongoing- Freeze window scheduling
- Stakeholder communication
- Validation procedures
- Go-live coordination
Data Transfer Methods & Optimization
Online Transfer
High-speed network transfer with compression and encryption for smaller datasets.
- • Up to 10 TB datasets
- • Real-time monitoring
- • Incremental sync
- • Bandwidth optimization
Offline Transfer
Physical device shipping for large datasets with secure handling and tracking.
- • 10+ TB datasets
- • Encrypted devices
- • Chain of custody
- • Faster than network
Hybrid Approach
Combination of methods optimized for different data types and priorities.
- • Mixed dataset sizes
- • Priority-based routing
- • Cost optimization
- • Flexible scheduling
Migration Sequencing Priorities
Change Freeze Windows
Pre-Migration Freeze
48 hours before data transfer begins
Migration Window
During active data transfer and validation
Post-Migration Validation
24 hours after go-live for monitoring
Rollback Window
72 hours for potential rollback decisions
Data Movement Success Metrics
Security and Compliance
Comprehensive security framework with encryption, access controls, and protected health information handling to ensure Supporting HIPAA Compliance throughout migration.
Encryption
End-to-end encryption for data protection
- AES-256 encryption at rest
- TLS 1.3 for data in transit
- Key management and rotation
- Hardware security modules
Access Controls
Identity and access management framework
- Multi-factor authentication
- Role-based access control
- Privileged access management
- Regular access reviews
PHI Handling
Protected health information safeguards
- Data classification and labeling
- Minimum necessary access
- Audit logging and monitoring
- Breach notification procedures
Compliance
Regulatory compliance frameworks
- Supporting HIPAA Compliance validation
- Regular compliance audits
- Documentation and evidence
Supporting HIPAA Compliance Framework
Administrative Safeguards
- Security officer designation
- Workforce training programs
- Access management procedures
- Incident response plans
Technical Safeguards
- Access control systems
- Audit controls and logging
- Data integrity controls
- Transmission security
Physical Safeguards
- Facility access controls
- Workstation security
- Device and media controls
- Environmental protections
Security Monitoring & Response
Real-time Threat Detection
24/7 monitoring with automated threat detection and response
Continuous Monitoring
Comprehensive logging and audit trail maintenance
Incident Response
Rapid response team with defined escalation procedures
Compliance Validation
Zero-Breach Migration Record
- 200+ healthcare migrations with zero security incidents
- 100% Supporting HIPAA Compliance validation success rate
- 24/7 security operations center monitoring

Resilience and Business Continuity
Comprehensive backup strategy, disaster recovery objectives, and failover testing to ensure continuous healthcare operations with minimal downtime.
Backup Strategy
Multi-tier backup approach with automated scheduling and validation
- Automated daily backups
- Point-in-time recovery
- Cross-region replication
- Backup integrity testing
Disaster Recovery
Comprehensive DR plan with defined objectives and procedures
- Hot standby environments
- Automated failover
- Recovery orchestration
- Regular DR testing
High Availability
Multi-zone deployment with load balancing and redundancy
- Multi-AZ deployment
- Load balancing
- Auto-scaling groups
- Health monitoring
Failover Testing
Regular testing to validate recovery procedures and objectives
- Quarterly DR drills
- Automated test scenarios
- Performance validation
- Documentation updates
Business Continuity Framework
Risk Assessment
Identify potential threats and vulnerabilities that could impact healthcare operations.
Recovery Planning
Develop detailed procedures for system recovery and business resumption.
Testing & Validation
Regular testing to ensure recovery procedures work as expected.
Continuous Improvement
Regular updates and improvements based on testing results and lessons learned.
Recovery Time Objectives (RTO)
Recovery Point Objectives (RPO)
Proven Business Continuity Results
Operations and Handover
Comprehensive operational setup with monitoring, logging, runbooks, and clearly defined roles and responsibilities for seamless post-migration operations.
Monitoring & Alerting
Comprehensive monitoring setup with proactive alerting
- Dashboard configuration
- Alert policy setup
- Escalation procedures
- Performance baselines
Logging & Auditing
Centralized logging with audit trail capabilities
- Log aggregation setup
- Retention policies
- Audit trail configuration
- Compliance reporting
Runbooks & Procedures
Detailed operational procedures and troubleshooting guides
- Standard operating procedures
- Troubleshooting guides
- Emergency procedures
- Change management process
Roles & Responsibilities
Clear definition of operational roles and accountability
- RACI matrix
- Contact directories
- Escalation paths
- Training materials
Operational Readiness Framework
Knowledge Transfer
Comprehensive training and documentation handover
Tool Configuration
Setup and configuration of operational tools
Process Validation
Testing and validation of operational procedures
Go-Live Support
Extended support during transition period
Operational Excellence Results
Cost Management and Optimization
Comprehensive cost optimization strategies with budgets, tagging, and continuous monitoring to maximize cloud ROI and minimize waste.
Resource Right-Sizing
25-35%Optimize compute and storage resources based on actual usage
- CPU and memory optimization
- Storage tier optimization
- Instance type recommendations
- Auto-scaling configuration
Reserved Capacity
30-50%Leverage reserved instances and savings plans for predictable workloads
- Reserved instance planning
- Savings plan optimization
- Commitment analysis
- Usage forecasting
Automated Scheduling
40-60%Schedule non-production resources to run only when needed
- Development environment scheduling
- Test environment automation
- Backup optimization
- Idle resource detection
Cost Monitoring
15-25%Continuous monitoring and alerting for cost anomalies
- Budget alerts and thresholds
- Cost anomaly detection
- Departmental chargeback
- Regular cost reviews
Cost Governance Framework
Tagging Strategy
Comprehensive resource tagging for cost allocation and tracking across departments and projects.
- • Department allocation
- • Project tracking
- • Environment classification
- • Owner identification
Budget Management
Proactive budget monitoring with alerts and automated actions to prevent cost overruns.
- • Monthly budget limits
- • Threshold alerts
- • Automated shutdowns
- • Approval workflows
Cost Reporting
Regular cost analysis and reporting with actionable insights for continuous optimization.
- • Weekly cost reviews
- • Trend analysis
- • Optimization recommendations
- • Executive dashboards
Cost Optimization Timeline
Immediate (0-30 days)
Right-sizing, unused resource cleanup
15-25% savingsShort-term (1-3 months)
Reserved capacity, scheduling automation
30-40% savingsMedium-term (3-6 months)
Architecture optimization, modernization
40-50% savingsLong-term (6+ months)
Cloud-native transformation, automation
50%+ savingsCost Monitoring Tools
Proven Cost Optimization Results
Ready to Get Started?
Contact our team to learn how our Cloud Migration Strategy Services can support your needs and improve your efficiency.
Call us now: +1 (951) 622-8126
